How to Choose the Right Access Control Software
However, with the wide range of access control software options available on the market, choosing the right one for your specific needs can be a daunting task. Making the wrong choice can lead to security vulnerabilities, operational inefficiencies, and wasted investments. That's why it's essential to carefully consider various factors and follow a systematic access control system design guide when evaluating and selecting an access control solution.
In this comprehensive blog post, we'll dive deep into the world of access control software, exploring the key features, considerations, and best practices you should keep in mind to make an informed decision. Whether you're a security professional, facility manager, system integrator, or business owner, this guide will provide you with valuable insights and actionable tips to help you navigate the complex landscape of access control systems.
So, let's embark on this journey together and learn how to choose the right access control software for your organization's unique security requirements. By the end of this post, you'll be well-equipped with the knowledge and tools necessary to design and implement an effective and efficient access control system that meets your needs today and scales with your growth in the future.
Understanding Access Control Systems
At its core, an access control system is a security solution that regulates who can enter or exit specific areas of a building or facility. It does this by authenticating the identity of individuals and granting or denying access based on predefined permissions and rules. Access control systems typically consist of hardware components like card readers, door locks, and controllers, as well as software that manages the system's configuration, user database, and access logs.
There are several types of access control systems, each with its own advantages and use cases:
- Discretionary Access Control (DAC): In this model, the owner or administrator of the protected resource (e.g., a file or folder) determines who can access it and what permissions they have. DAC is commonly used in file sharing and operating systems.
- Mandatory Access Control (MAC): MAC is a stricter approach where access is granted based on predefined security labels assigned to both users and resources. The system enforces these rules, and even resource owners cannot override them. MAC is often used in high-security environments like military or government facilities.
- Role-Based Access Control (RBAC): RBAC grants access based on a user's role within the organization. Permissions are assigned to roles, and users inherit those permissions when they are assigned to a role. RBAC simplifies access management and is widely used in corporate settings.
- Attribute-Based Access Control (ABAC): ABAC evaluates various attributes of users, resources, and environmental conditions to make access decisions. These attributes can include user roles, location, time of day, device type, and more. ABAC offers granular control and is suitable for complex, dynamic environments.
- Risk-Adaptive Access Control: This approach dynamically adjusts access privileges based on the assessed risk level of each access request. It considers factors like user behavior, device security posture, and network conditions to determine the risk and applies appropriate access policies.
Understanding these different types of access control systems will help you identify which model best aligns with your organization's security requirements and IT infrastructure. Keep in mind that many modern access control software solutions offer a combination of these approaches to provide a more comprehensive and flexible security framework.
Now that we have a basic grasp of access control systems let's explore the key features and capabilities you should look for when evaluating access control software options.
Key Features to Look for in Access Control Software
When choosing an access control software solution, it's essential to consider a range of features that can enhance the security, usability, and scalability of your system. Here are some key features to look for:
- Integration with Hardware Components: Your access control software should seamlessly integrate with a wide range of hardware devices, such as card readers, biometric scanners, door locks, and controllers. Look for software that supports open standards and protocols like OSDP (Open Supervised Device Protocol), which allows for interoperability between different brands and models of hardware.
- User Management and Provisioning: The software should provide an intuitive interface for managing user accounts, credentials, and access permissions. It should allow you to easily add, modify, and remove users, assign them to groups or roles, and define granular access rights based on factors like job function, location, and time of day.
- Real-Time Monitoring and Alerts: An effective access control system should offer real-time monitoring capabilities, allowing you to track user activity, door status, and system events as they occur. Look for software that provides customizable alerts and notifications, so you can quickly respond to potential security breaches or anomalies.
- Reporting and Analytics: Robust reporting and analytics features are crucial for auditing, compliance, and optimization purposes. Your access control software should generate detailed logs of user activity, access attempts, and system changes. It should also provide intuitive dashboards and visualizations to help you identify patterns, trends, and areas for improvement.
- Mobile Access and Remote Management: In today's mobile-first world, it's important to choose access control software that supports mobile credentials and remote management. Look for solutions that allow users to access doors and gates using their smartphones or wearables, and enable administrators to manage the system remotely via web-based or mobile apps.
- Scalability and Flexibility: As your organization grows and evolves, your access control system should be able to scale and adapt accordingly. Choose software that can handle a large number of users, doors, and sites, and offers the flexibility to customize access rules, integrate with other systems (e.g., video surveillance, HR databases), and expand functionality through APIs or plugins.
- Cybersecurity and Encryption: With access control systems increasingly connected to IT networks and the cloud, cybersecurity is a top concern. Ensure that the software you choose employs strong encryption, secure communication protocols, and regular security updates to protect against hacking attempts and data breaches.
- Compliance and Certifications: Depending on your industry and location, you may need to comply with specific security standards or regulations, such as HIPAA, FISMA, or GDPR. Look for access control software that is certified and compliant with relevant standards to ensure that your system meets legal and ethical requirements.
- User Experience and Support: Finally, consider the user experience and support offered by the access control software provider. The software should have an intuitive, user-friendly interface that minimizes training time and reduces errors. Additionally, look for vendors that provide comprehensive documentation, training resources, and responsive customer support to help you get the most out of your investment.
By carefully evaluating these key features and capabilities, you'll be better equipped to select an access control software solution that meets your organization's unique security needs and business objectives. In the next section, we'll discuss some important considerations to keep in mind when designing your access control system.
Designing Your Access Control System
Designing an effective access control system involves more than just choosing the right software. It requires careful planning, consideration of your organization's specific needs, and alignment with best practices in physical security. Here are some key factors to consider when designing your access control system:
- Assess Your Security Requirements: Start by conducting a thorough assessment of your organization's security needs. Consider factors like the size and layout of your facilities, the number and types of users, the sensitivity of your assets, and any regulatory or compliance requirements. This assessment will help you determine the appropriate level of security and the specific features you need in your access control system.
- Define Access Zones and Levels: Based on your security assessment, define distinct access zones within your facilities, such as public areas, employee-only spaces, and restricted or high-security areas. Assign appropriate access levels to each zone based on the principle of least privilege, granting users only the access they need to perform their job functions.
- Choose the Right Credential Technology: Select a credential technology that balances security, convenience, and cost. Options include traditional keys and cards (e.g., magnetic stripe, proximity, smart cards), biometric identifiers (e.g., fingerprints, facial recognition), and mobile credentials (e.g., smartphone apps, Bluetooth tokens). Consider factors like the level of security required, user adoption, and integration with your existing systems.
- Plan for Scalability and Integration: Design your access control system with future growth and integration in mind. Choose software and hardware components that can scale to accommodate an increasing number of users, doors, and sites. Additionally, consider how your access control system will integrate with other security and building systems, such as video surveillance, intrusion detection, and visitor management.
- Implement Strong Authentication and Encryption: To protect against unauthorized access and data breaches, implement strong authentication methods and encryption protocols. This may include multi-factor authentication (e.g., card + PIN, biometric + mobile app), secure communication channels (e.g., HTTPS, VPN), and data encryption at rest and in transit.
- Establish Clear Policies and Procedures: Develop and document clear policies and procedures for managing your access control system. This should include guidelines for user provisioning and deprovisioning, credential issuance and revocation, access level assignment, and incident response. Regularly review and update these policies to ensure they remain relevant and effective.
- Train and Educate Users: Provide comprehensive training and education to your users on the proper use of the access control system. This should cover topics like credential management, tailgating prevention, and reporting lost or stolen credentials. Foster a culture of security awareness and encourage users to report any suspicious activity or potential vulnerabilities.
- Monitor and Audit System Activity: Regularly monitor and audit your access control system to detect and respond to potential security incidents. This may involve reviewing access logs, investigating anomalous events, and conducting periodic penetration testing to identify weaknesses in your system. Use the insights gained from monitoring and auditing to continuously improve your access control policies and procedures.
By following these best practices and considering these key factors, you can design an access control system that effectively balances security, usability, and scalability. In the next section, we'll explore some common challenges and pitfalls to avoid when implementing and managing your access control system.
Common Challenges and Pitfalls to Avoid
Implementing and managing an access control system can present various challenges and potential pitfalls. By being aware of these common issues and taking proactive steps to address them, you can ensure a smoother deployment and more effective operation of your system. Here are some key challenges and pitfalls to avoid:
- Inadequate Planning and Budgeting: One of the most common mistakes organizations make is failing to properly plan and budget for their access control system. This can lead to underestimating the costs of hardware, software, installation, and ongoing maintenance, resulting in project delays or cost overruns. To avoid this pitfall, conduct thorough research, consult with experienced professionals, and develop a detailed project plan and budget that accounts for all necessary expenses.
- Neglecting Cybersecurity: As access control systems become increasingly connected to IT networks and the cloud, they also become more vulnerable to cyber threats. Neglecting cybersecurity can expose your system to hacking attempts, data breaches, and other malicious activities. To mitigate these risks, follow best practices in network security, such as using strong encryption, secure communication protocols, and regular security updates. Additionally, conduct periodic vulnerability assessments and penetration testing to identify and address potential weaknesses.
- Poor User Adoption and Training: Another common challenge is poor user adoption and training. If users find the access control system difficult to use or understand, they may resort to workarounds or bypass security measures altogether. To avoid this pitfall, choose software with a user-friendly interface and provide comprehensive training and support to users. Regularly communicate the importance of following proper security procedures and encourage feedback to identify areas for improvement.
- Inadequate Maintenance and Updates: Access control systems require regular maintenance and updates to ensure optimal performance and security. Neglecting these tasks can lead to system failures, vulnerabilities, and compliance issues. To avoid this pitfall, establish a regular maintenance schedule that includes tasks like firmware updates, battery replacements, and performance testing. Additionally, stay informed about the latest security patches and updates from your software and hardware vendors, and apply them promptly.
- Lack of Integration and Interoperability: Many organizations struggle with integrating their access control system with other security and building systems, such as video surveillance, intrusion detection, and visitor management. This lack of integration can lead to silos of information, inefficiencies, and potential security gaps. To avoid this pitfall, choose access control software that supports open standards and APIs for integration. Work with experienced system integrators who can help you design and implement a cohesive security ecosystem.
- Insufficient Disaster Recovery and Business Continuity Planning: Access control systems are critical for maintaining the security and safety of your facilities. However, many organizations fail to plan for disaster recovery and business continuity in the event of a system failure or emergency. To avoid this pitfall, develop and regularly test a comprehensive disaster recovery plan that includes backup power sources, redundant hardware, and off-site data storage. Additionally, establish clear procedures for manual override and emergency access in case of system downtime.
- Ignoring Compliance and Regulatory Requirements: Depending on your industry and location, you may be subject to various compliance and regulatory requirements related to access control and data privacy. Ignoring these requirements can lead to legal and financial penalties, as well as reputational damage. To avoid this pitfall, stay informed about the latest regulations and standards that apply to your organization, such as HIPAA, FISMA, or GDPR. Choose access control software that is certified and compliant with relevant standards, and regularly audit your system to ensure ongoing compliance.
By being aware of these common challenges and pitfalls and taking proactive steps to address them, you can minimize risks, optimize performance, and maximize the value of your access control system investment. In the next section, we'll explore some real-world case studies and examples of successful access control system implementations.
Introducing XTEN-AV's X-DRAW: Automating Access Control System Design
As a system integrator, consultant, or engineer working on physical security or smart building projects, you understand the importance of efficient and accurate access control system design. Traditional methods of creating complex schematics and documentation can be time-consuming, error-prone, and limit collaboration. That's where XTEN-AV's X-DRAW comes in – a powerful audio visual (av) system design software and documentation platform that significantly enhances and automates the process of access control system design.
Here's how X-DRAW helps with automating access control system design, along with key features explained:
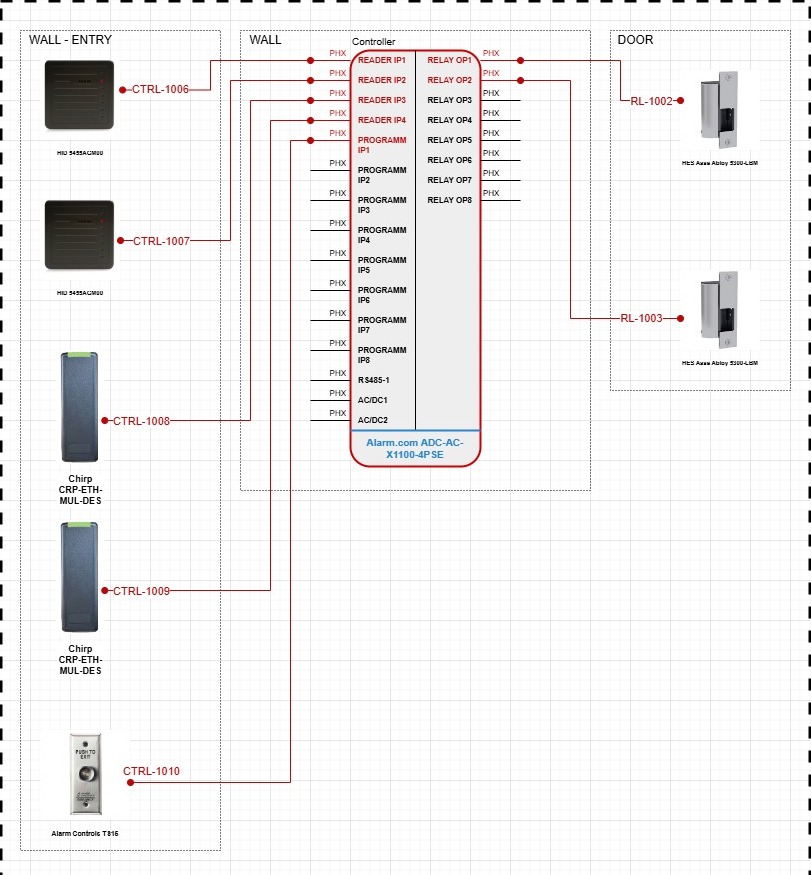
1. Intelligent Block Diagramming
X-DRAW allows you to create automated signal flow and system diagrams, including access control infrastructure, by simply dragging and dropping devices from a library. This helps eliminate the manual effort of building complex access control schematics from scratch. You can visually design layouts showing door readers, controllers, door locks, cabling, power supplies, and networks.The smart connections between devices are auto-routed, minimizing design errors and time
2. Product Libraries with Real Devices
XTEN-AV offers an extensive database of real-world devices from thousands of manufacturers. This includes:
- Card readers, access panels, electric strikes, biometric scanners, and network switches
- Fire alarm interface modules, surveillance components, and power sources
3. Auto-Generated Documentation
One of the most powerful automation features is that X-DRAW creates all the necessary design documentation in real time, such as:
- Bill of Materials (BOM) – precise list of components used in your design
- Wiring diagrams – automated wiring paths between access components
- CAD-level schematics – floor plan overlays with device locations
- Proposal-ready documents – exports for client presentations or RFPs
4. Integration With Floor Plans
You can upload architectural floor plans (PDF or CAD), and place access control components (e.g., door readers, magnetic locks, control panels) directly onto them. This helps:
- Align system design with the physical layout
- Plan door-by-door access and control zones
- Visualize access points, emergency exits, and zones with restricted access
5. Signal & Power Path Calculations
X-DRAW automates the logic of access control system design by validating signal and power flow:
- Ensures voltage compatibility across connected devices
- Verifies control panel capacity
- Calculates total power consumption for backup power systems
6. Cloud-Based Collaboration
Since XTEN-AV is cloud-based, multiple team members (engineering, sales, project management) can collaborate in real time. Changes to the access control system design can be:
- Reviewed and commented on live
- Version-controlled
- Exported or shared instantly with stakeholders
7. Sales Enablement and Proposals
X-DRAW isn't just a design tool — it helps security integrators turn designs into proposals:
- Convert access control system designs into automated quotes
- Generate sales-ready PDFs with branding, pricing, and solution overviews
- Export into formats for bid submissions or approval processes
8. System Templates & Reusability
For companies or designers working on multi-site projects (e.g., retail chains, hospitals, office buildings), X-DRAW allows you to:
- Create reusable templates for access control designs
- Apply consistent device configurations across projects
- Rapidly customize for each location, saving design time
Case Studies and Real-World Examples
To better understand the benefits and best practices of access control systems, let's explore some real-world case studies and examples of successful implementations across various industries and applications.
Case Study 1: Healthcare Facility
A large healthcare facility with multiple buildings and departments implemented an access control system to improve security, comply with HIPAA regulations, and streamline visitor management. The system included the following features:
- Proximity card readers and smart cards for secure, contactless access
- Integration with the facility's HR database for automated user provisioning and deprovisioning
- Role-based access control (RBAC) to restrict access based on job function and department
- Visitor management system with self-service kiosks and temporary badges
- Real-time monitoring and alerts for unauthorized access attempts or tailgating
- Audit trails and reporting for compliance and incident investigation
The results:
- Reduced unauthorized access incidents by 90%
- Improved HIPAA compliance and passed all audits
- Streamlined visitor check-in process and reduced wait times by 50%
- Increased staff productivity and satisfaction with user-friendly interface
Case Study 2: Corporate Office
A global corporation with multiple office locations implemented an access control system to enhance security, improve operational efficiency, and support a flexible work environment. The system included the following features:
- Mobile credentials and smartphone-based access for employees and visitors
- Cloud-based management platform for centralized control and remote administration
- Integration with the company's IT systems for single sign-on (SSO) and user management
- Attribute-based access control (ABAC) to dynamically adjust permissions based on user roles, location, and time of day
- Occupancy tracking and space utilization analytics for optimizing office layout and resource allocation
- Touchless access and hygiene features for a safe and healthy workplace
The results:
- Reduced security incidents and unauthorized access by 95%
- Improved operational efficiency and reduced administrative overhead by 40%
- Supported a flexible, hybrid work model with secure remote access
- Enhanced employee experience and satisfaction with convenient, mobile-based access
- Optimized office space utilization and reduced real estate costs by 20%
Case Study 3: Educational Institution
A university campus with multiple buildings, classrooms, and labs implemented an access control system to improve safety, streamline access management, and support a diverse user population. The system included the following features:
- Multi-factor authentication with smart cards and biometric readers for high-security areas
- Integration with the university's student information system (SIS) for automated enrollment and access provisioning
- Role-based access control (RBAC) to manage access for students, faculty, staff, and visitors
- Scheduled access and time-based restrictions for classrooms, labs, and events
- Emergency lockdown and mass notification capabilities for crisis situations
- Mobile app for campus navigation, access requests, and virtual credentials
The results:
- Improved campus safety and security with granular access control and real-time monitoring
- Reduced administrative burden and errors with automated user management and provisioning
- Enhanced student and faculty experience with convenient, mobile-based access and navigation
- Supported flexible scheduling and space utilization for classrooms, labs, and events
- Demonstrated compliance with safety regulations and improved emergency preparedness
These case studies demonstrate the diverse applications and benefits of access control systems across different industries and use cases. By leveraging the right features, integrations, and best practices, organizations can significantly improve security, compliance, efficiency, and user experience with a well-designed access control solution.
Frequently Asked Questions (FAQs)
- What is the difference between access control software and hardware? Access control software is the program that manages the access control system, including user management, access permissions, and system configuration. Access control hardware refers to the physical components of the system, such as card readers, door locks, controllers, and sensors.
-
- How do I determine the appropriate level of security for my access control system? The appropriate level of security depends on factors like the sensitivity of your assets, regulatory requirements, and potential threats. Conduct a thorough risk assessment to identify your security needs and consult with experienced professionals to design a system that balances security, usability, and cost.
- Can I integrate my access control system with other security systems? Yes, many modern access control software solutions support integration with other systems, such as video surveillance, intrusion detection, and visitor management. Look for software that offers open APIs and supports industry standards like ONVIF and OSDP for seamless integration and interoperability.
- How do I ensure the cybersecurity of my access control system? To ensure the cybersecurity of your access control system, follow best practices such as using strong encryption, secure communication protocols, and regular security updates. Implement network segmentation, firewalls, and multi-factor authentication to prevent unauthorized access. Regularly conduct vulnerability assessments and penetration testing to identify and address potential weaknesses.
- What should I consider when choosing between on-premises and cloud-based access control software? The choice between on-premises and cloud-based access control software depends on factors like your IT infrastructure, budget, and scalability needs. On-premises solutions offer more control and customization but require dedicated hardware and IT resources. Cloud-based solutions provide flexibility, scalability, and lower upfront costs but may have ongoing subscription fees and rely on internet connectivity.
- How often should I update and maintain my access control system? Regular updates and maintenance are crucial for ensuring the performance, security, and compliance of your access control system. Establish a maintenance schedule that includes tasks like firmware updates, battery replacements, and performance testing at least quarterly or as recommended by your vendor. Stay informed about the latest security patches and updates, and apply them promptly to address any vulnerabilities.
- What are some best practices for managing user access and credentials? Best practices for managing user access and credentials include:
- Implementing a formal user provisioning and deprovisioning process
- Following the principle of least privilege and granting access based on job roles
- Using strong, unique passwords or multi-factor authentication
- Regularly auditing user access rights and revoking unnecessary permissions
- Promptly deactivating credentials for terminated employees or contractors
- Educating users on proper credential management and security practices
- How can I ensure the scalability and future-proofing of my access control system? To ensure the scalability and future-proofing of your access control system, choose software and hardware components that can accommodate growth in users, doors, and sites. Look for solutions that support open standards, modular architecture, and flexible integration options. Consider the vendor's roadmap and track record of innovation to ensure they can meet your evolving needs and stay ahead of industry trends.
By addressing these common questions and concerns, you can make informed decisions and implement an access control system that effectively meets your organization's security, compliance, and operational requirements.
Conclusion
In today's complex and ever-evolving security landscape, choosing the right access control software is a critical decision that can significantly impact the safety, efficiency, and success of your organization. By understanding the key features, design considerations, and best practices outlined in this comprehensive guide, you can navigate the selection process with confidence and implement a system that aligns with your unique needs and objectives.
Remember to start by assessing your security requirements, considering factors like asset sensitivity, user roles, and regulatory compliance. Evaluate software options based on essential features like hardware integration, user management, real-time monitoring, reporting, and cybersecurity. Design your system with scalability, interoperability, and user experience in mind, and establish clear policies and procedures for system management and user training.
Throughout the implementation and operation of your access control system, stay vigilant against common challenges and pitfalls, such as inadequate planning, poor cybersecurity, and lack of maintenance. Regularly review and update your system to address evolving threats, incorporate new technologies, and ensure ongoing compliance and effectiveness.
By following the guidance and insights provided in this blog post, you can unlock the full potential of access control software to create a secure, efficient, and user-friendly environment for your organization. Whether you're safeguarding critical assets, streamlining operations, or enhancing the user experience, a well-designed access control system is a vital investment in the success and resilience of your business.